Cynergy Platform
Next Generation EASM Powered by Automated Remediation
Fortify Your Defence Against External Threats
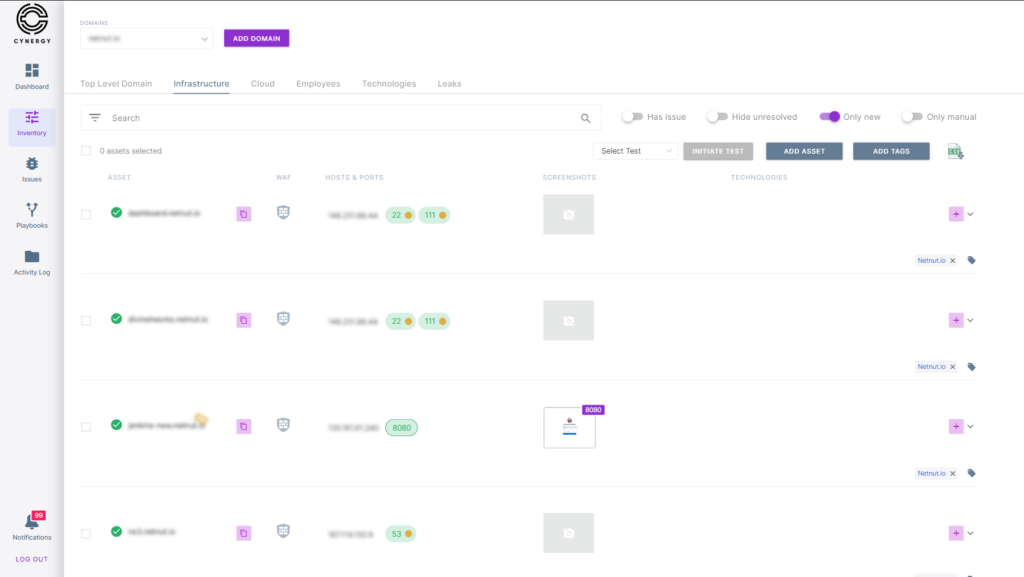
Cynergy’s platform is designed to help you protect your organization from external threats by managing your attack surface. With Cynergy, you can discover assets and vulnerabilities, validate vulnerabilities, and remediate them in a timely and efficient manner.
Cynergy uses advanced technology and techniques to scan and monitor your external attack surface, giving you a complete picture of your organization’s security posture. With the Cynergy platform, you can proactively identify and fix vulnerabilities before they can be exploited, reducing the risk of a data breach or cyber attack. Protect your organization and your sensitive data with our comprehensive external attack surface management platform.
Next Gen Attack Surface Management
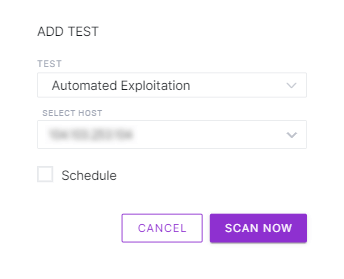
Validate vulnerabilities on a continuous basis to ensure your security posture is always up to date.
Continuous Automated Validation and Remediation
Proactively discover and protect your organization's digital assets and infrastructure from external threats.
Protect based on priority
Context is king, and with Cynergy, you get the most contextualized information about the discovered assets. Once combining the asset context with the associated issues (Vulnerabilities or misconfigurations) Cynergy uses advanced proprietary machine learning models combined with industry standards such as CVSS and EPSS models, to efficiently prioritize the vulnerabilities and make your teams more efficient.
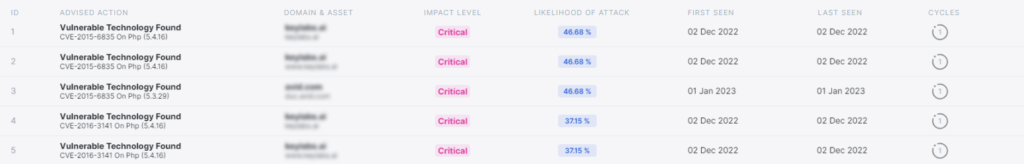
Eliminate the noise
Traditional EASM and 3rd party assessment tools are generating many false positives or insufficient identifications of assets. This is because such platforms rely on passive scanning and gathering of information from various APIs without correlating and validating the identified assets. Unlike traditional platforms, Cynergy is a Next Gen EASM, and as such it continuously validates the identified assets actively. And ties the assets with the organization based on advanced correlation rules.
Control the change
Your organization’s attack surface is constantly changing, instances are added and removed, storage is added and exposed, and new websites and applications are added for mass consumption. And your organization is using more and more SaaS products and ShadowIT components.
Cynergy Next Gen EASM allows you to monitor the change and identify the anomalies and exposures that may lead to the next breach.